How To Set Up Dynamic Reporting Security Access
Article Highlights:
- Keep data and report access in the hands of those who need it.
- These three layers of security help manage Dynamic Reporting permissions.
Dynamic Reporting is a powerful tool for creating custom reports in ERA-IGNITE using existing system data. To keep data and report access in the hands of only those who need it, there are three layers of security for Dynamic Reporting in the Security Maintenance application. These can be set on the individual User ID or User Group level for greater efficiency and consistency with security permissions.
Pull Up a Security Record
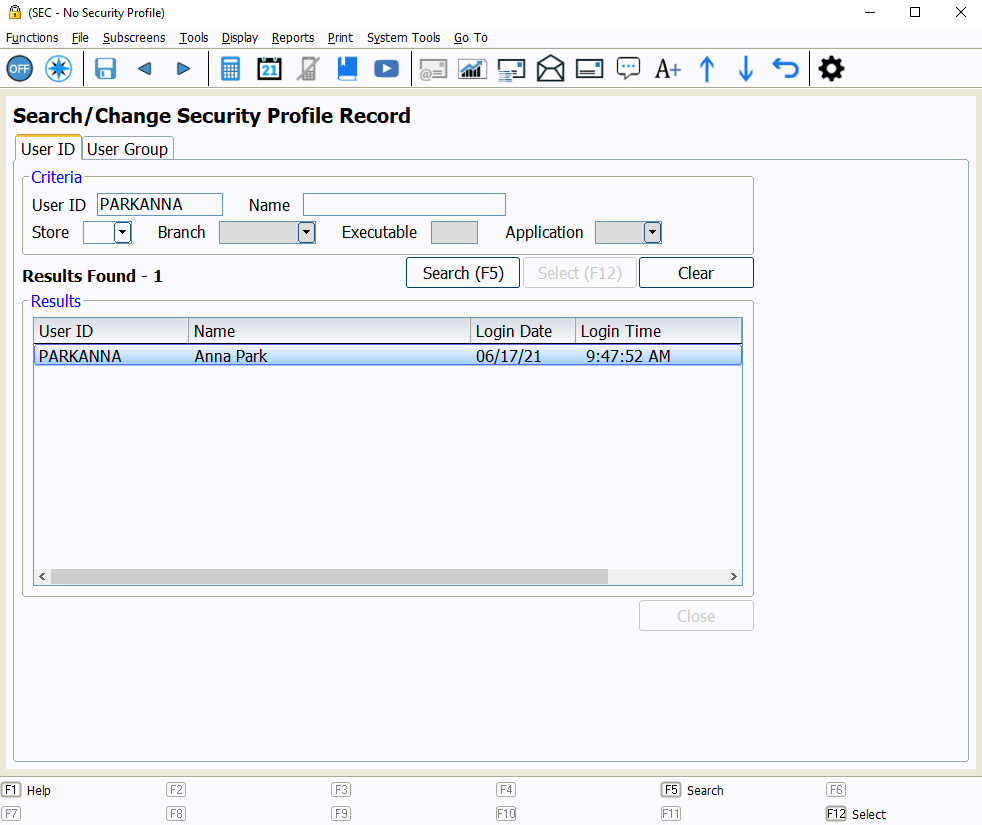
To look up a profile record, access the Search/Change Security Profile Record screen in the Security Maintenance application. Select the appropriate tab, User ID or User Group, depending on the type of record you need to access. Enter any search criteria, such as the User ID or Name, in the Criteria section and select Search (F5). Double-click or select and press ENTER to open the security record.
1. Store and Application Access
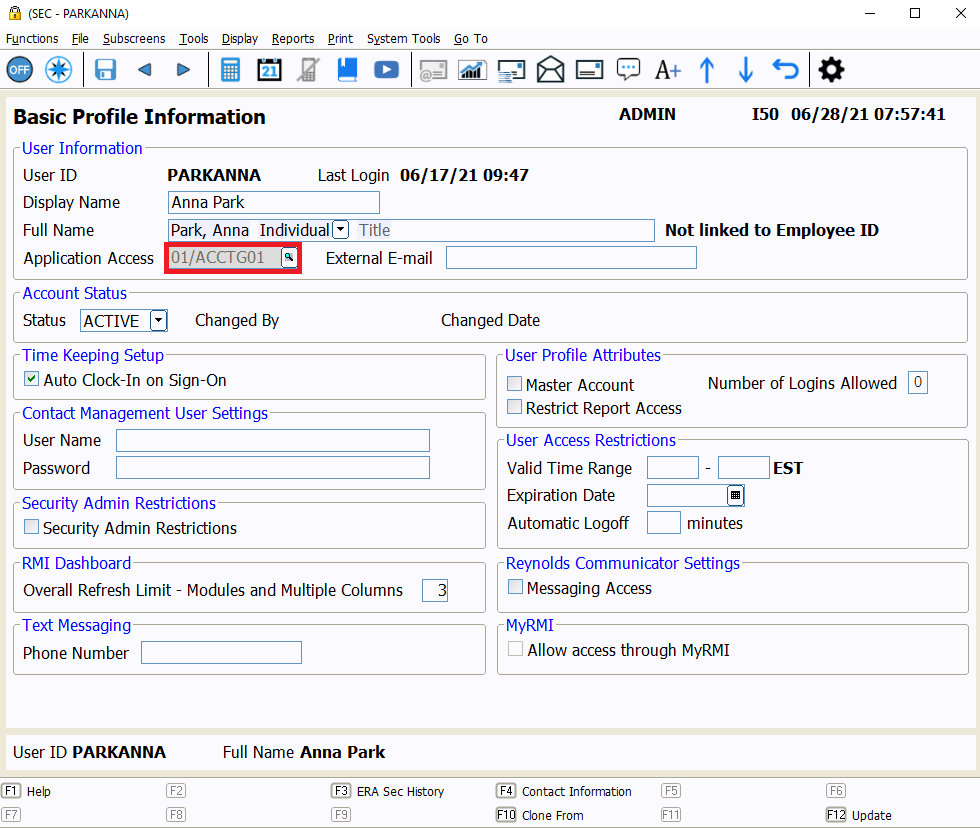
The first layer of security is store and application access. Each User ID can have customized access to the data of the stores and branches that apply to the individual. To give a User ID access, go to the Basic Profile Information subscreen within the User ID security record. Once there, select the lookup icon from the Application Access field.
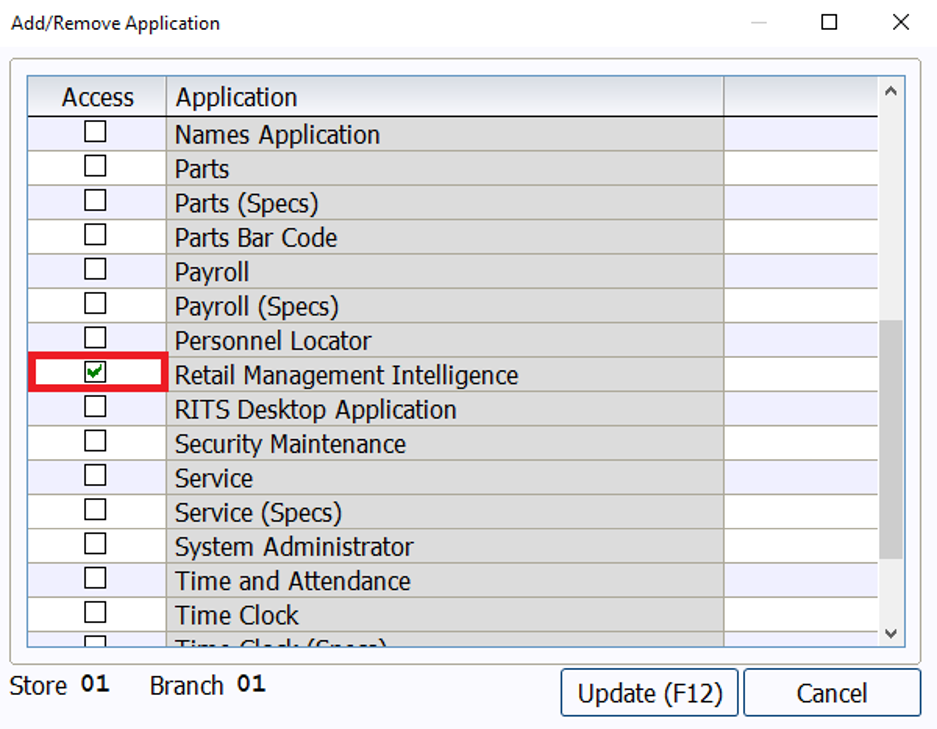
In the Application Access window, expand the permissions for the store with the plus icon next to the store name. Then, select the Access checkbox for any relevant applications within the appropriate branches, and select OK (F12).
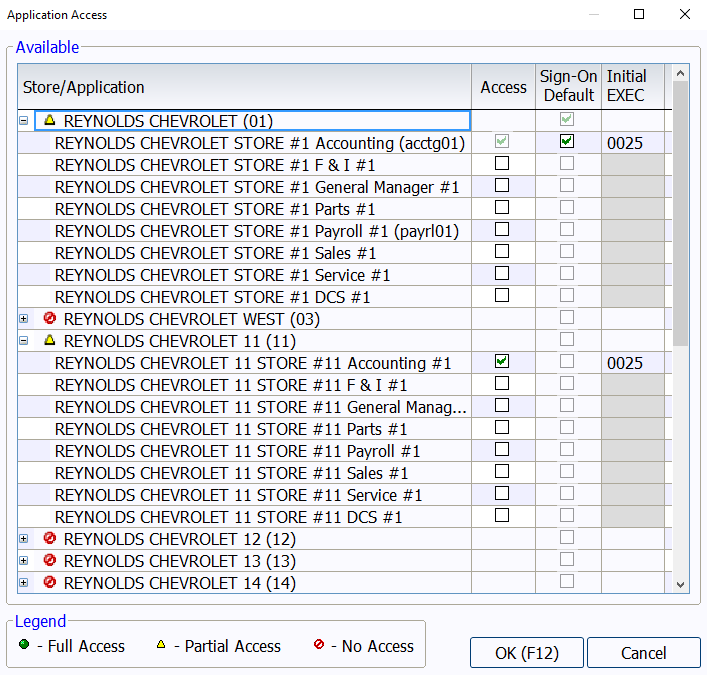
Note, User Groups are not given store and application access via the Application Access window. User Groups can be given access to the necessary stores and branches from the Security Access subscreen or the Enterprise Security Management subscreen.
2. Security Access
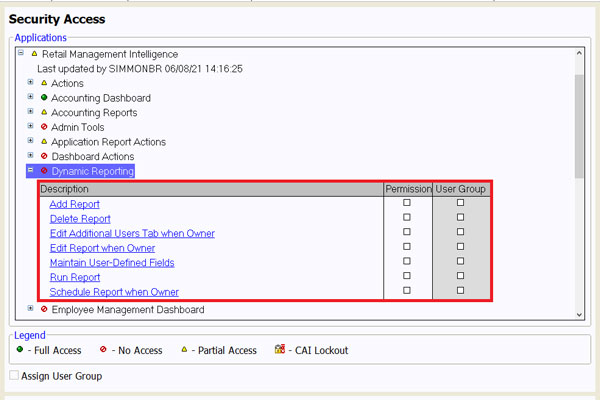
For the second layer, the User ID or User Group needs access to Retail Management Intelligence. This can be granted in the Security Access subscreen. If the User ID or User Group does not have Retail Management Intelligence listed on the Security Access subscreen, select (F5) Add/Remove Application. Next, select the Access checkbox for Retail Management Intelligence, then Update (F12).
On the Security Access screen, under Retail Management Intelligence → Dynamic Reporting, specific security permissions can be set for Dynamic Reporting. Select the checkboxes in the permission column for each necessary security item. Each User ID should only be given as much access as necessary to accomplish the tasks for their job role; not every user needs access to every security permission.
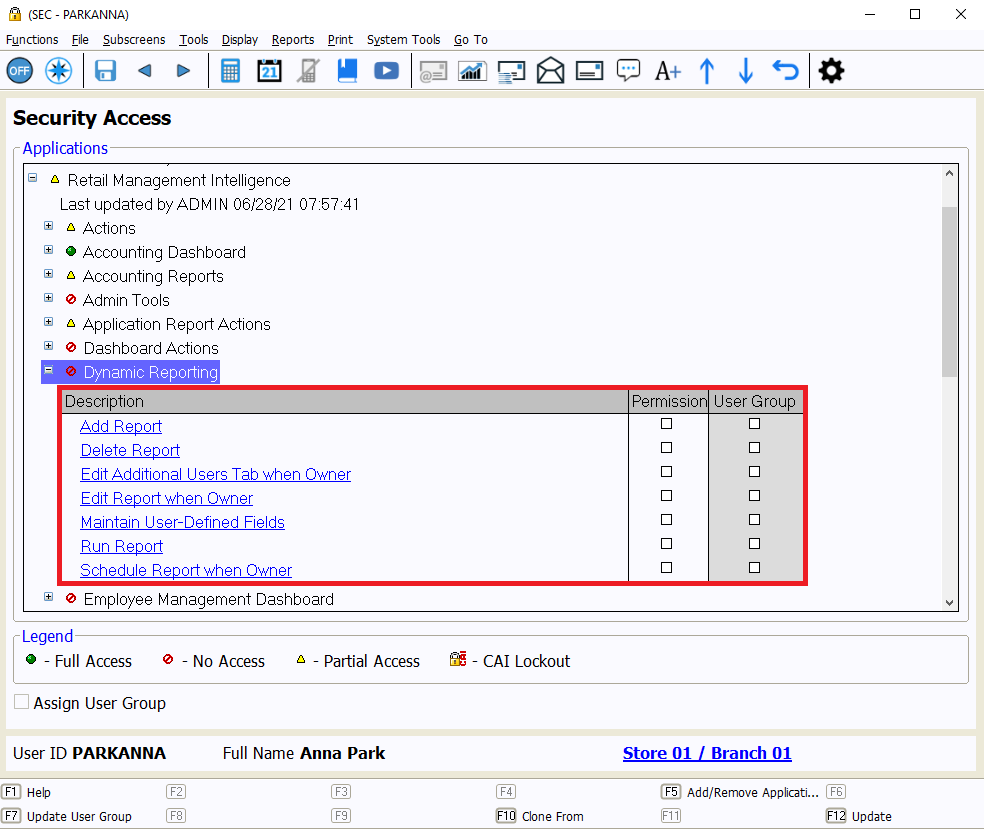
Permissions for Dynamic Reporting should be granted in each relevant store and branch. For those with multiple stores or branches, these permissions can also be managed from the Enterprise Security Management subscreen instead.
3. Data Set Security
The final layer of security is Data Set security. The Data Set you use dictates which fields are available to be used in a dynamic report. On the Dynamic Reporting Data Set Security subscreen, Data Sets are organized by Run Area. A user can be given access to some or all Data Sets within each Run Area for the selected store and branch.
There is also a checkbox to grant access to all Data Sets within a store/branch for those who need complete access to all Data Sets, but it is recommended that users are only given access to the specific data sets they need for their role.
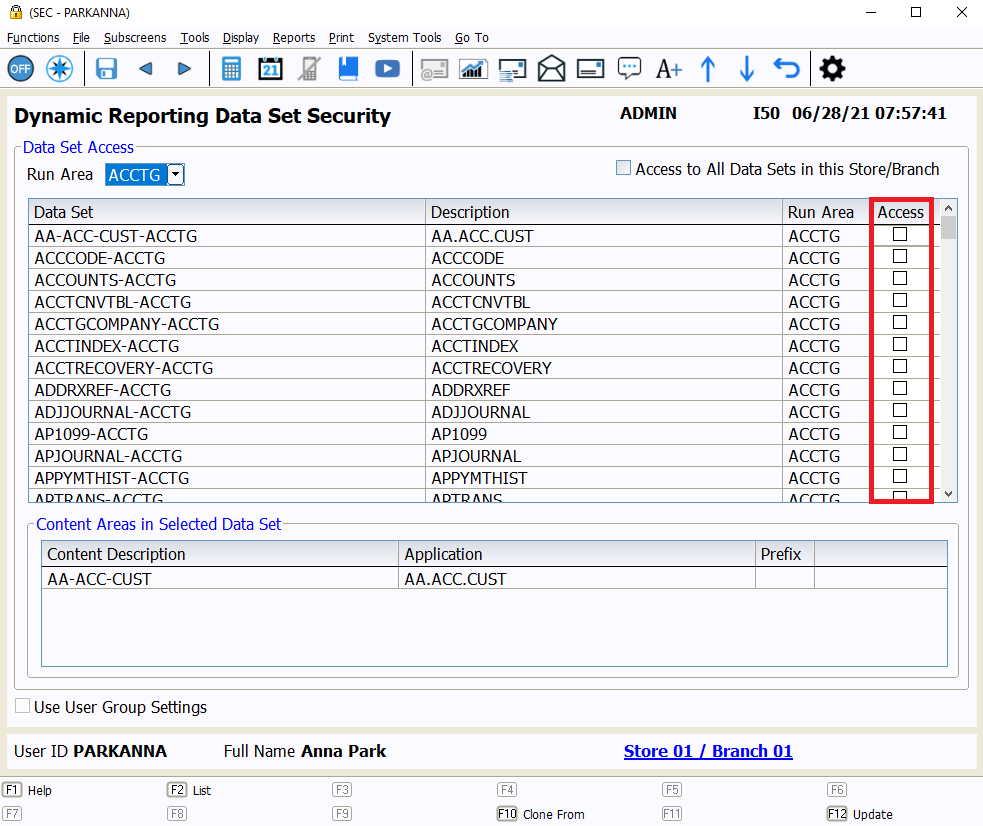
Permissions for Dynamic Reporting Data Sets should be granted in each relevant store and branch. As with Security Access, these permissions can also be managed from the Enterprise Security Management subscreen for those with multiple stores and branches.
When appropriate security permissions are granted to users, Dynamic Reporting is a useful, flexible tool for users to craft unique reports within ERA-IGNITE.
For more ERA-IGNITE training opportunities, check out Reynolds Software Education for upcoming webinars and classes.
Related Articles:
This article was written by Angelica Yensi, a software education representative. The ERA-IGNITE toolbar, positioned at the top of your ERA-IGNITE screen, offers easy access…
Keyboard shortcuts can do wonders for your everyday tasks. While there are default hotkeys throughout most computer systems, ERA-IGNITE has additional ones to make your…
This article was written by Rachel McCutchen, a Software Education Representative. When you are working in the Accounting journal screens ask yourself, what am I…
When you customize your software, you can help streamline your operations.